Introduction
In "WhatsApp, FB Messenger, iMessage, government; life not so private after all!", we were shocked by the revelation that 66% of all requests being done for user data by governments globally from Big Tech (Microsoft, Meta, Google, Apple) are being met.
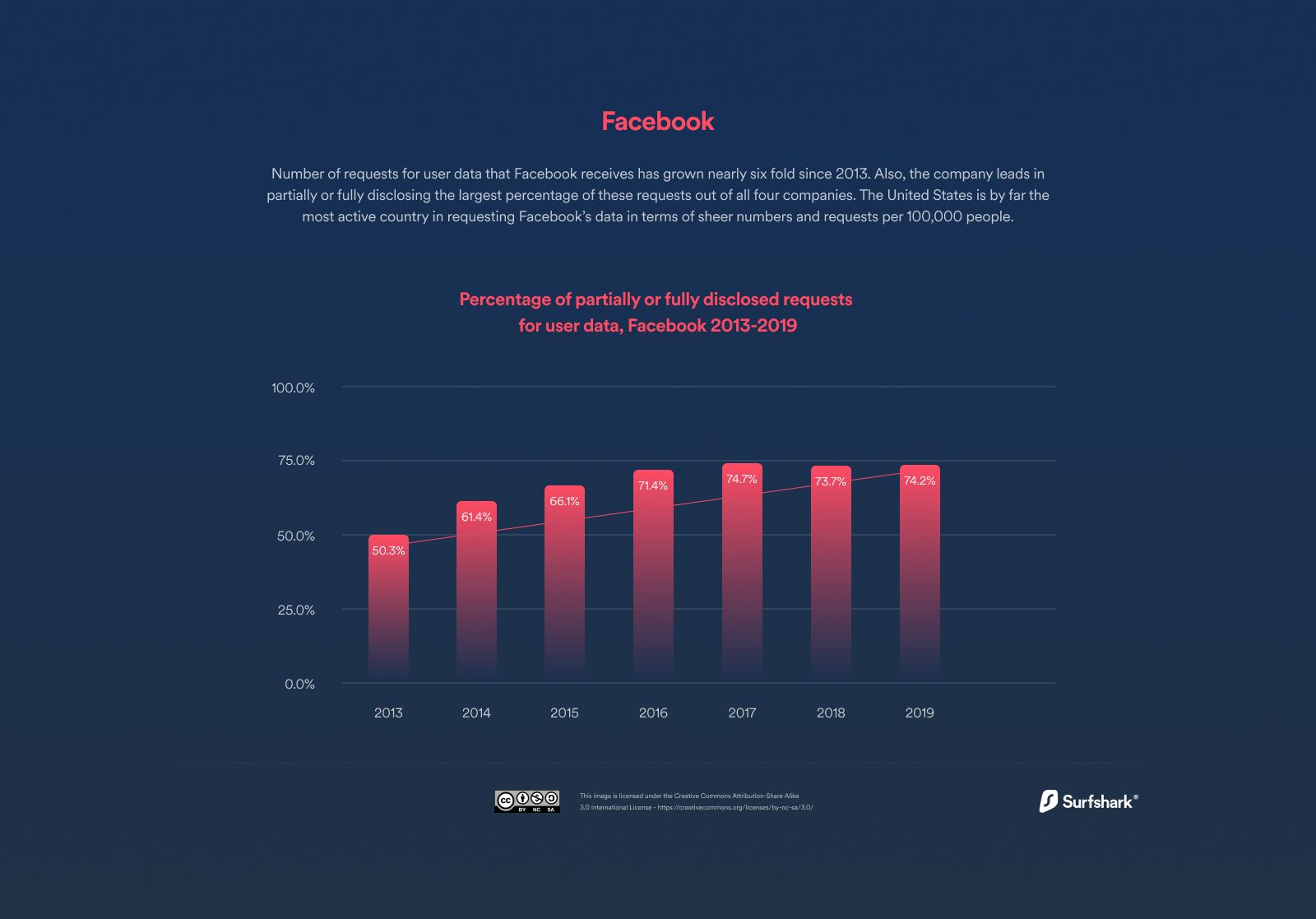
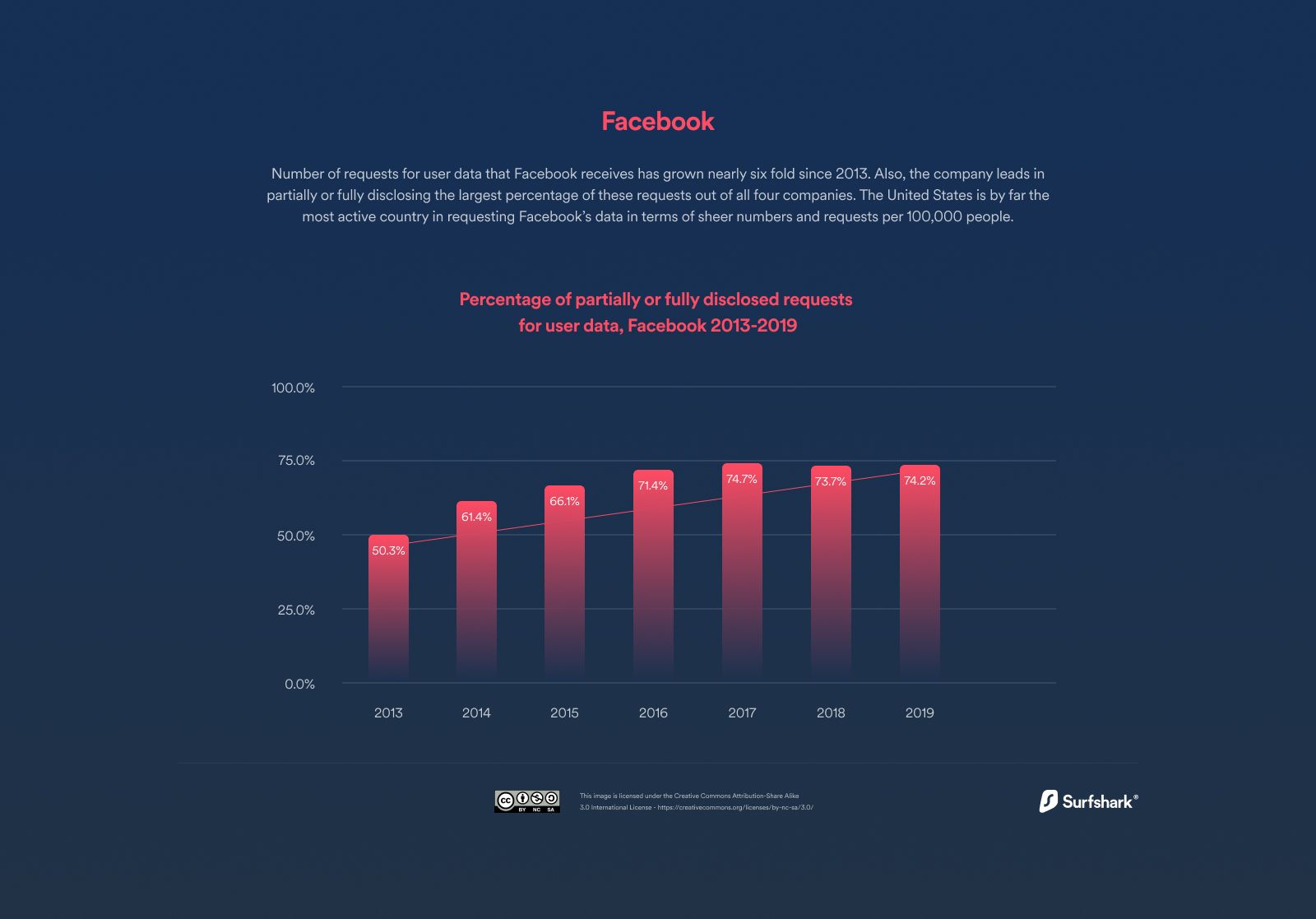
Did you know that the amount of fully or partially disclosed requests for user data from authorities grew by 213% since 2013!
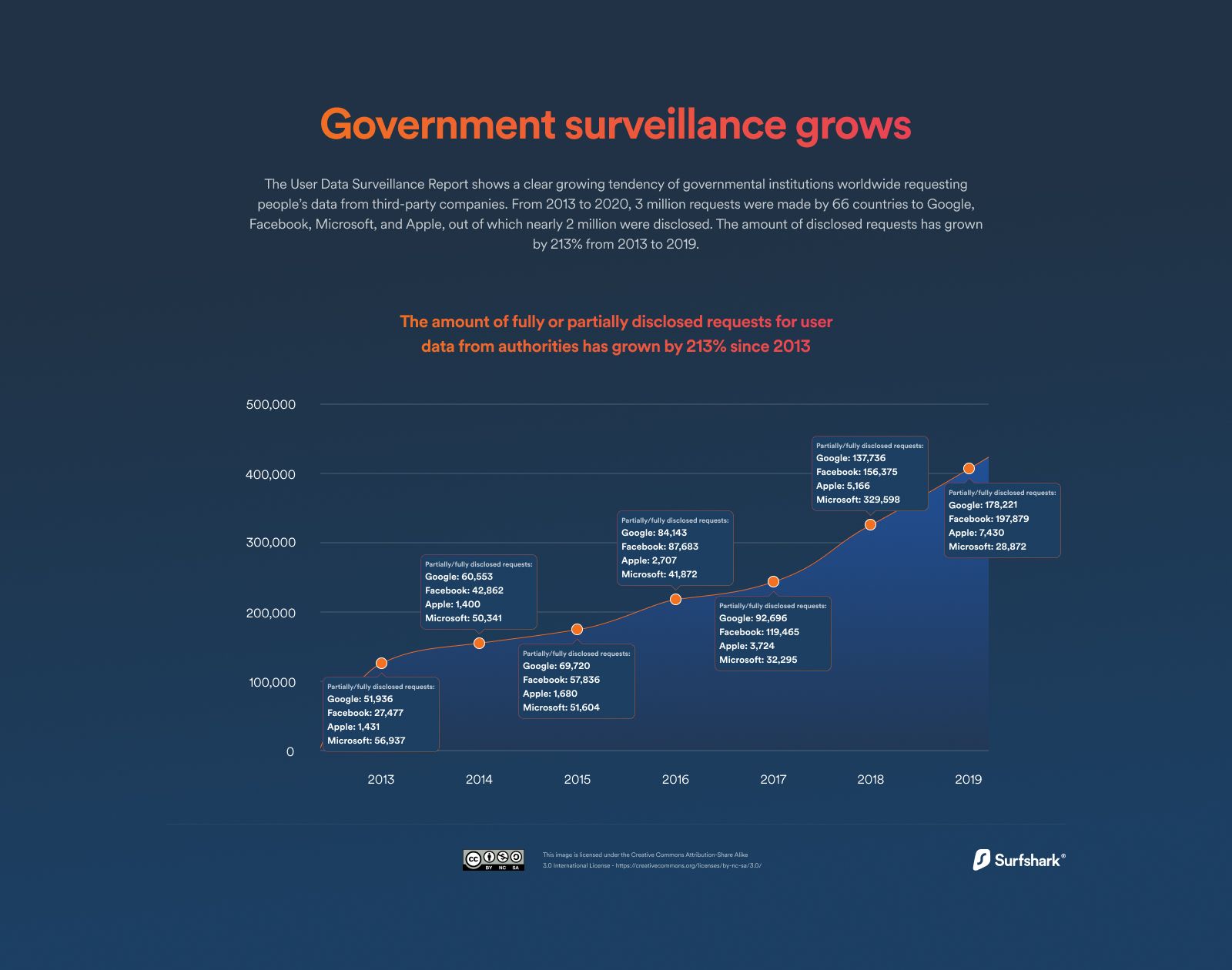
This means information about you is potentially being transferred and shared with regulatory bodies 66% of the times it is requested, at an ever-increasing rate!.
In this post, we explore:
- The sources of data around this 66% (incredibly eye-opening)
- Links you can use to find out how many requests your government is making!
- Share even more shocking information around how governments can access data lawfully across a broader set of applications, including WhatsApp, iMessage, Line, Signal, Telegram, Viber, WeChat, Wickr etc.
Law enforcement
New IT rules, applicable to large social media platforms and Big Tech, including WhatsApp, Twitter, Facebook, Microsoft Teams, etc., are being pushed to allow governments to access user data (potentially including your direct messages).
We discussed the concerns around such access in "Does end-to-end encryption (E2EE) matter to you? Which side are you on?", driving new concerns over privacy, freedom of expression, and data abuse to drive personal agendas.
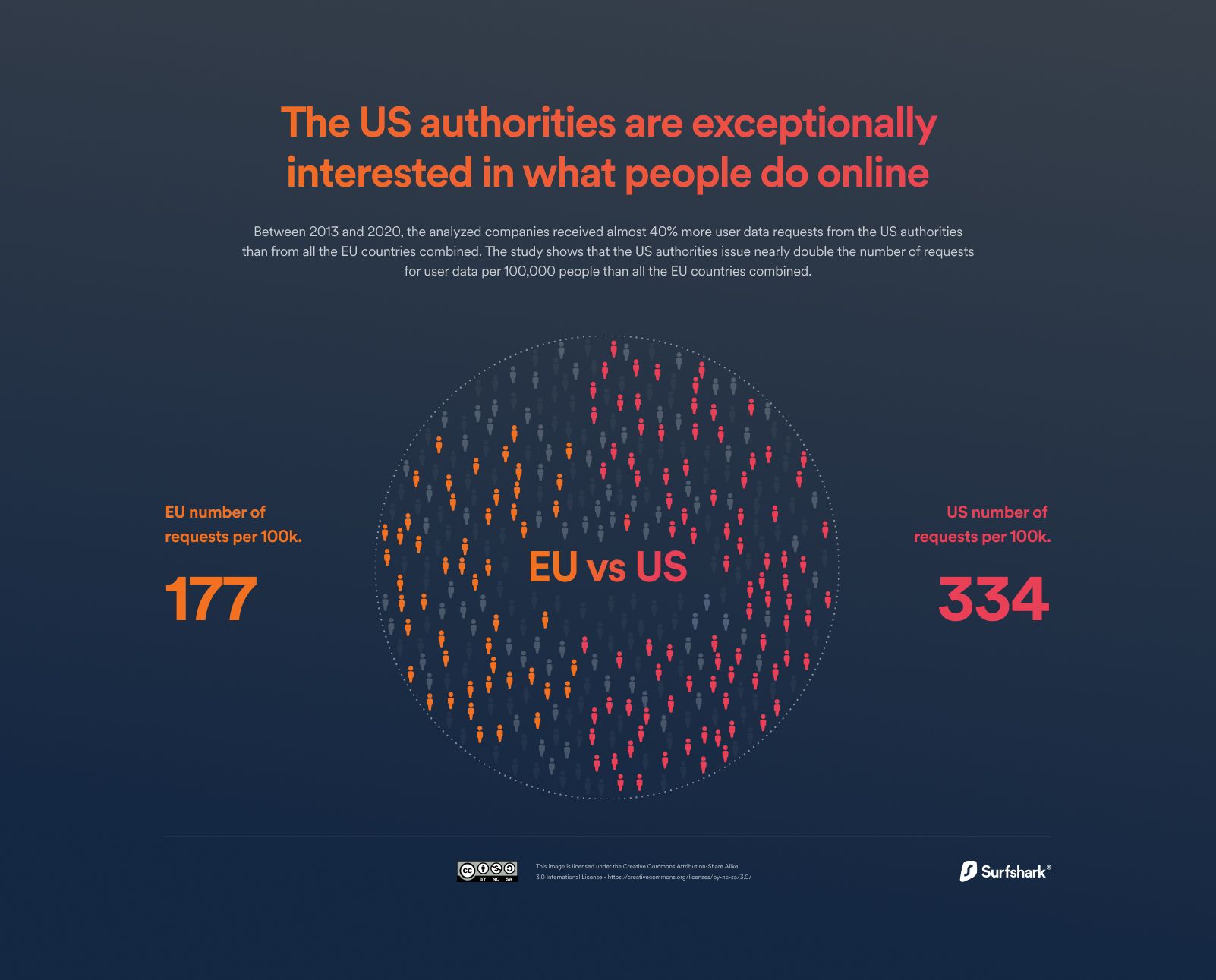
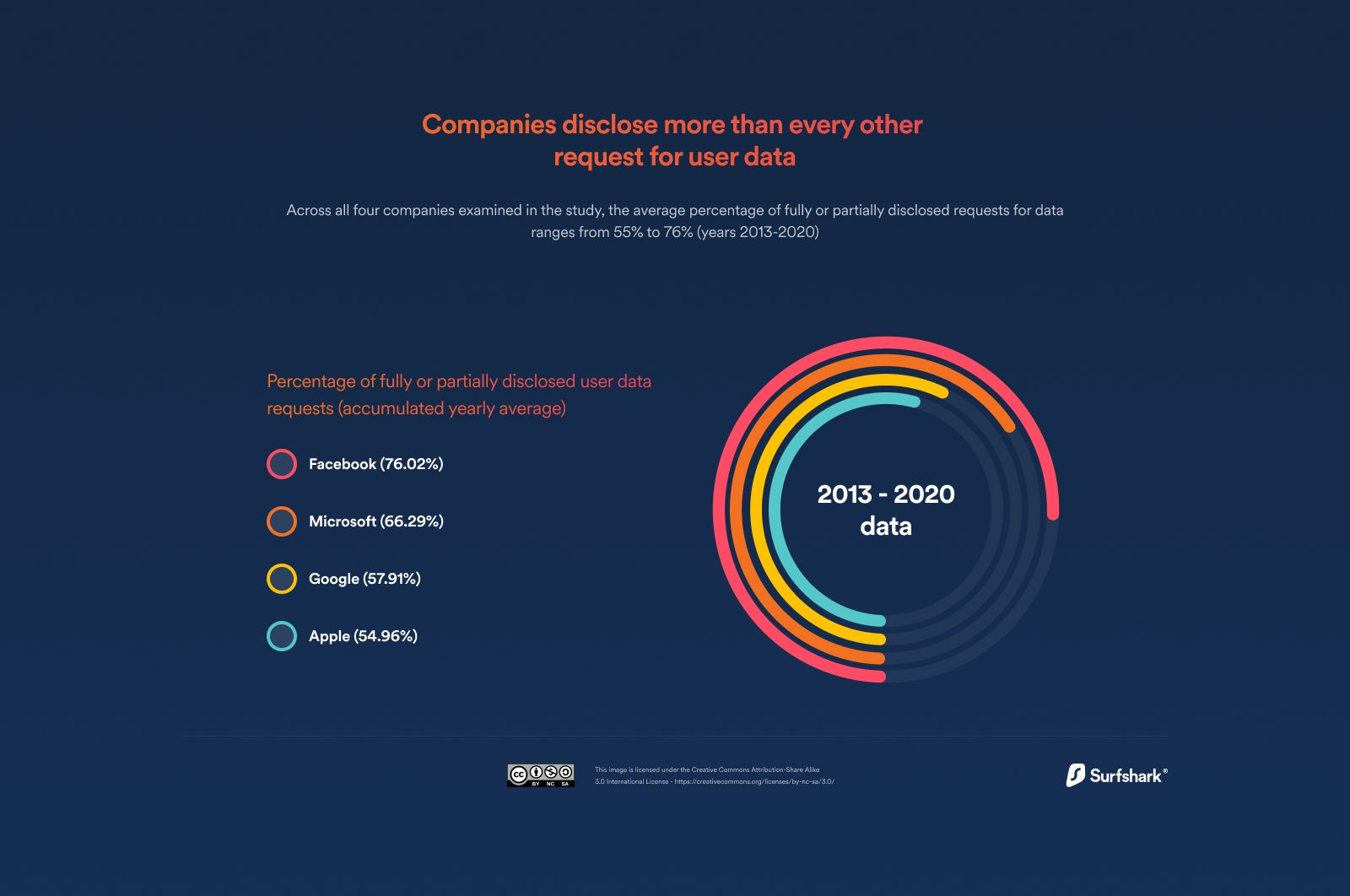
While organisations have publicly refuted making such capabilities available to governments, some leaks show something completely different!
A document allegedly obtained from the FBI claims how easy it is to harvest and access data from these services, including WhatsApp.
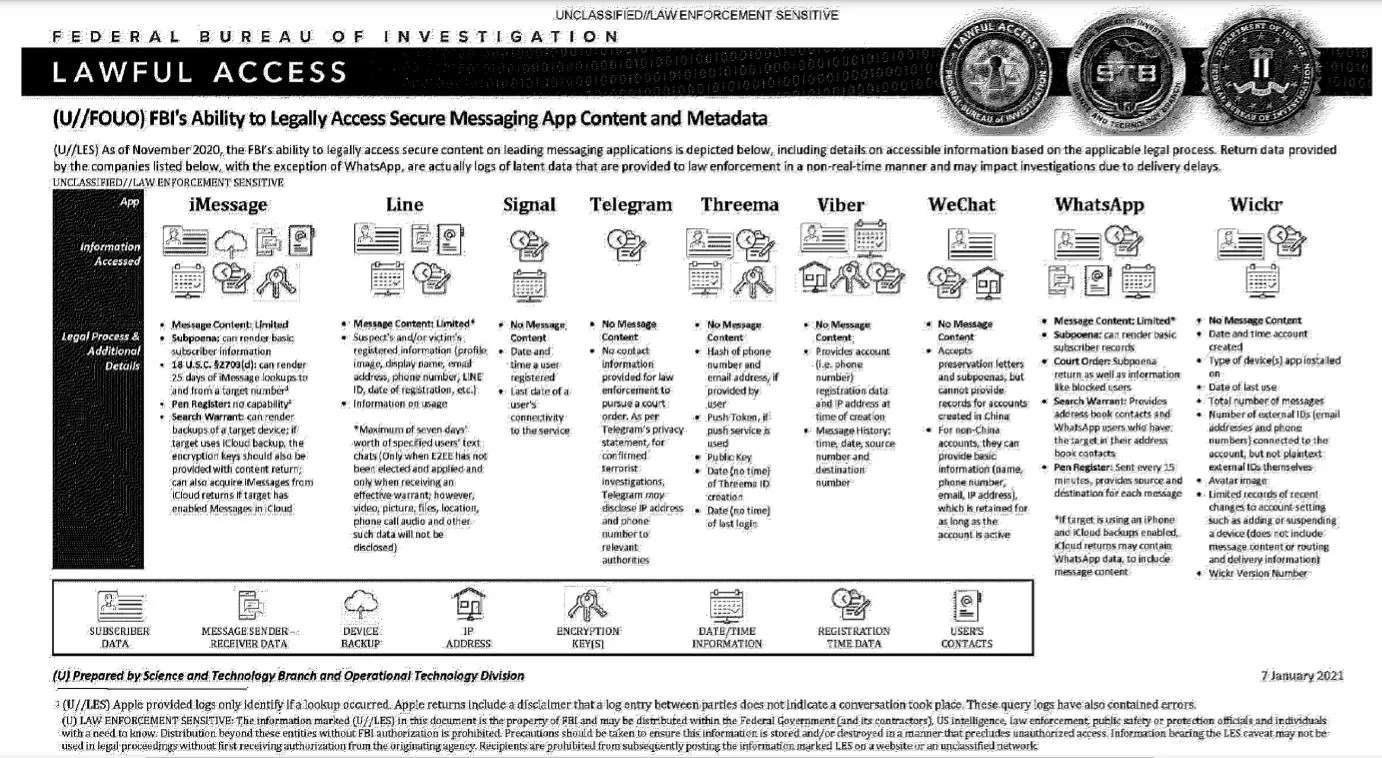
The document (titled "Lawful Access", dated Jan 7, 2021) describes that while messages are safe while being transferred, the weakness remains at the endpoints, where law enforcement agencies have multiple paths to gain lawful access to the data from these messaging solutions.
You can check it out more here: Document Detail - Property of the People.
The document highlights the value of the data that such solutions reveal. It also provides context around how WhatsApp will provide near-real-time information about a user and their activities when presented with a formal warrant, including address-book contacts and other meta-information that may be available. While identifying some limitations in the content of the data, the range of available data is still impressive, it flies in the face of the perception of privacy driven by technological terms such as end-to-end encryption.
This information needs to be taken in the context that an agency may request and access data and information from a broader set of services, including iMessage, iCloud, Instagram, Facebook Messenger etc.
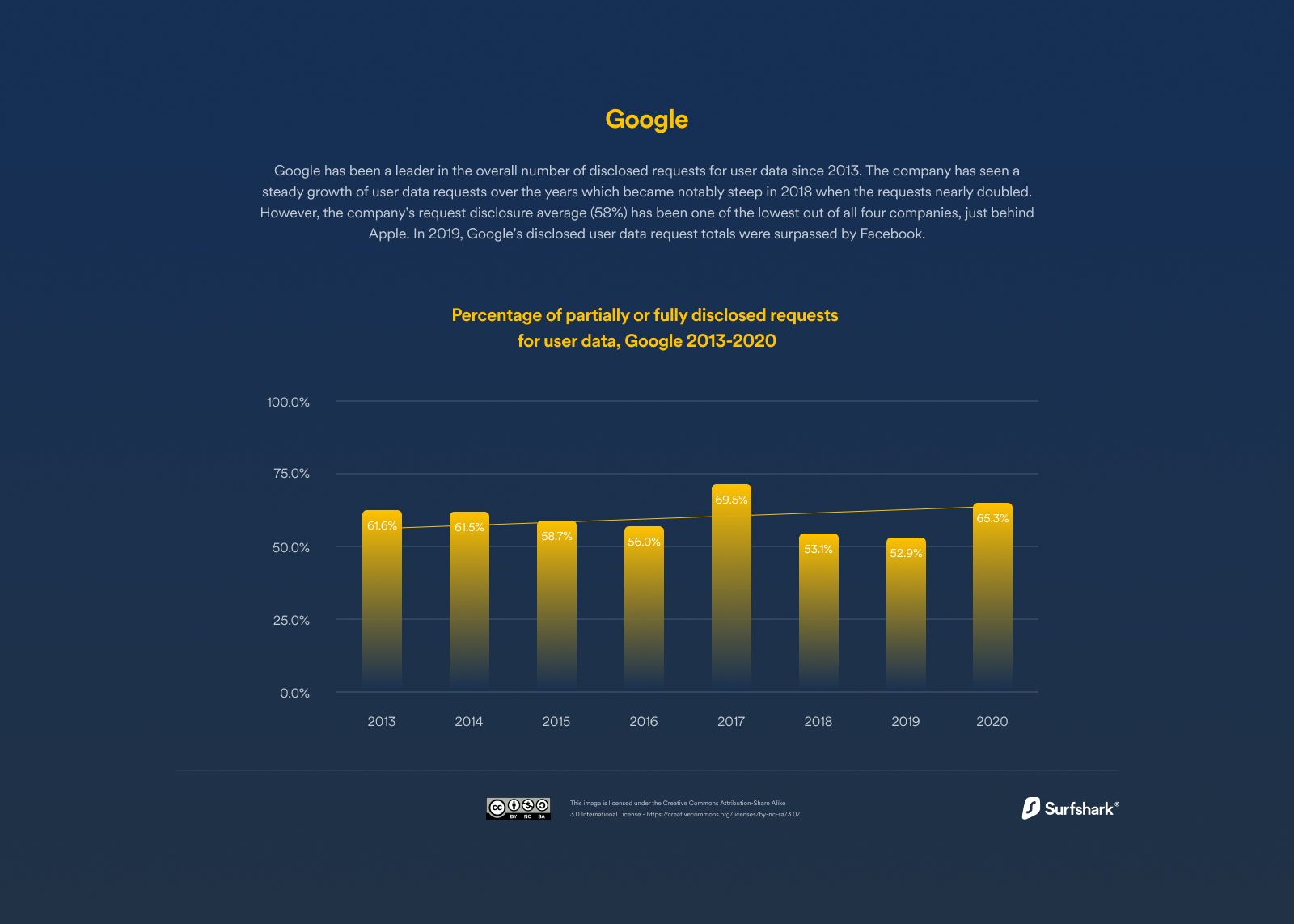
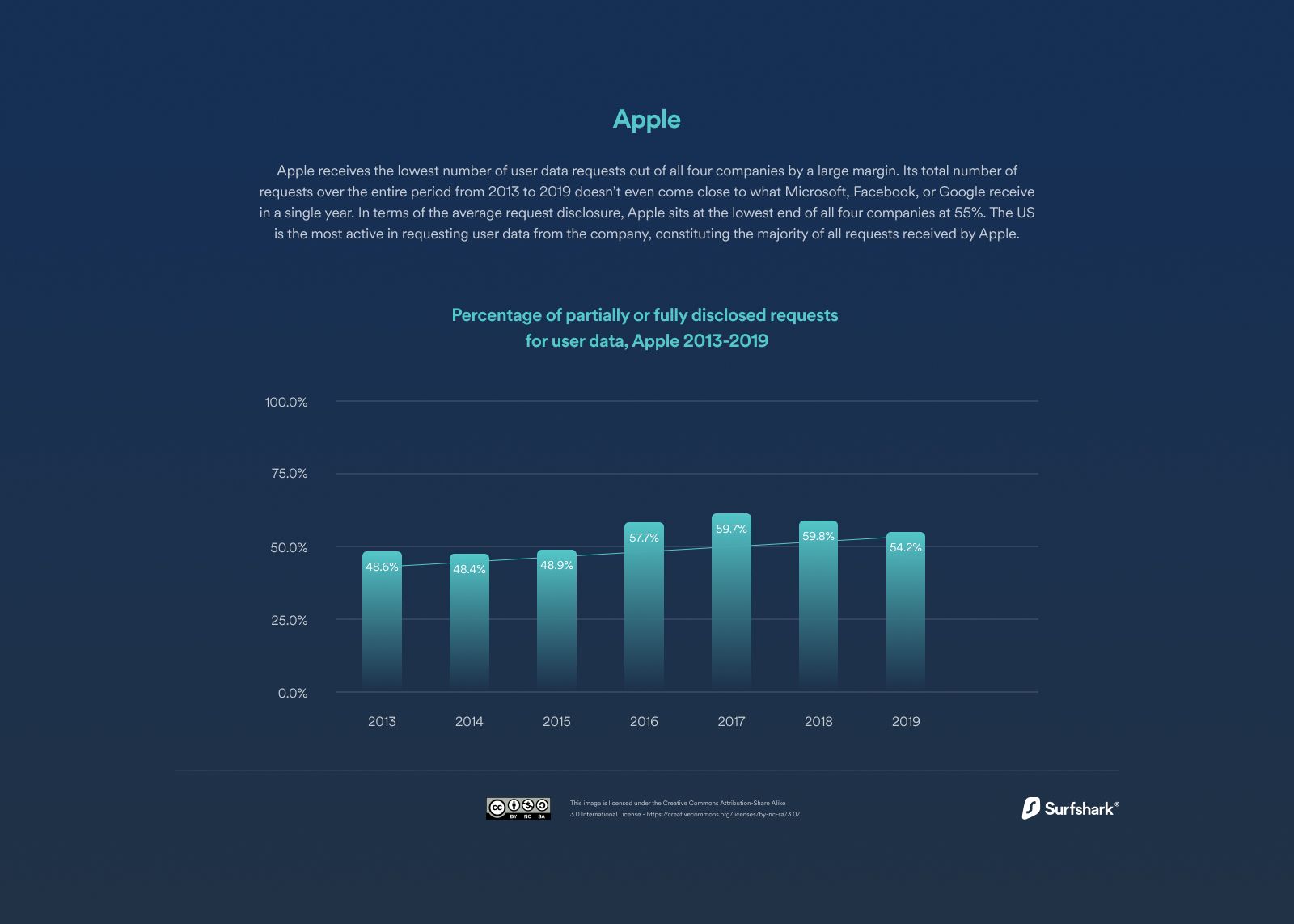
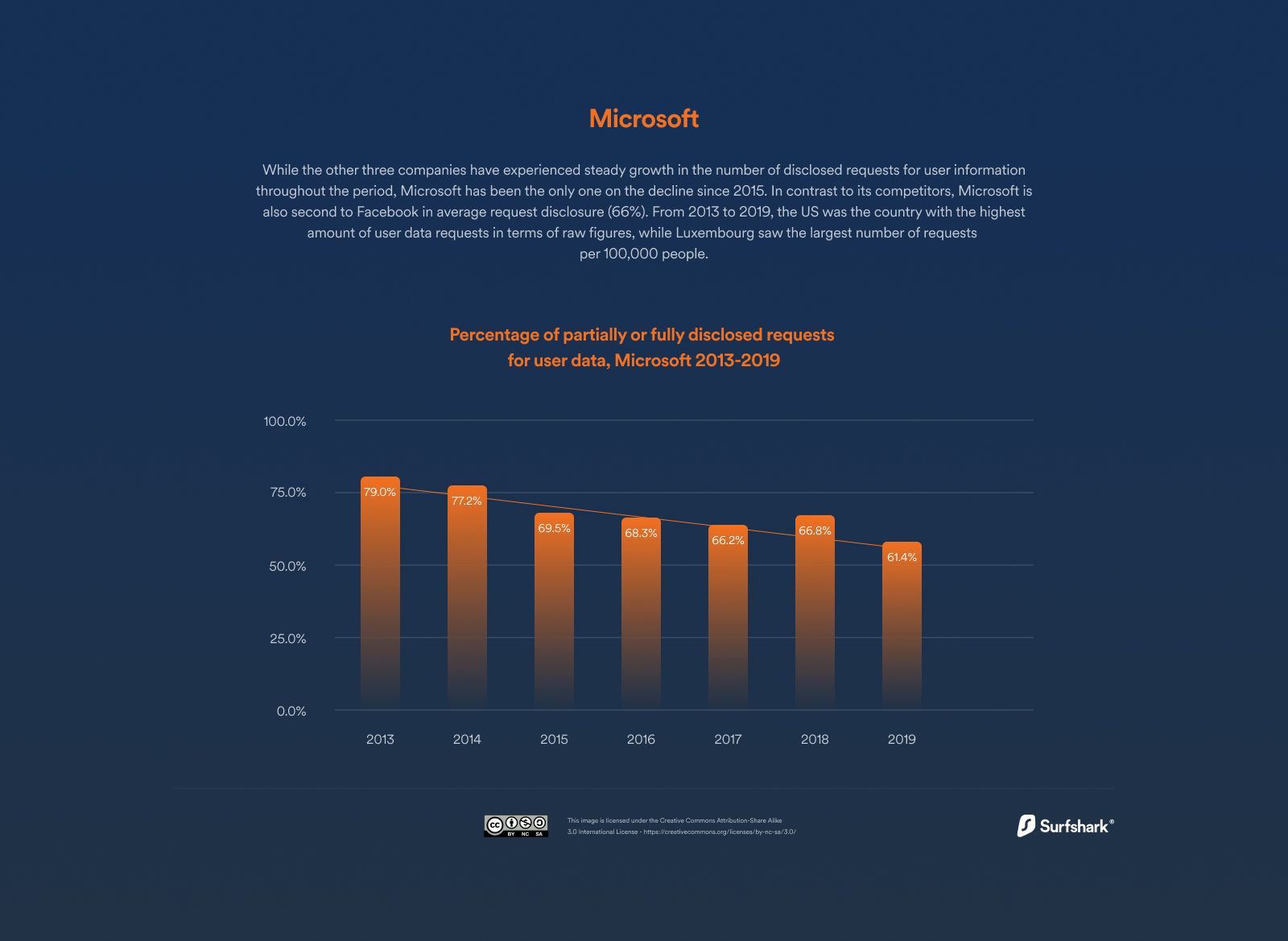
Other organisations, including Apple, Microsoft and Google, have shown that they provide similar support to government agencies that can either get customer consent or request a search warrant that will give them the required access.
The principle is that should you be suspected of a criminal offence, legal enforcement departments can serve an authentic warrant to the company.
But how many requests are made?
Using Facebook as an example (as the owner of WhatsApp), data indicates they received 191,013 law enforcement agency requests in 2020 across governments globally (Statista, 2020).
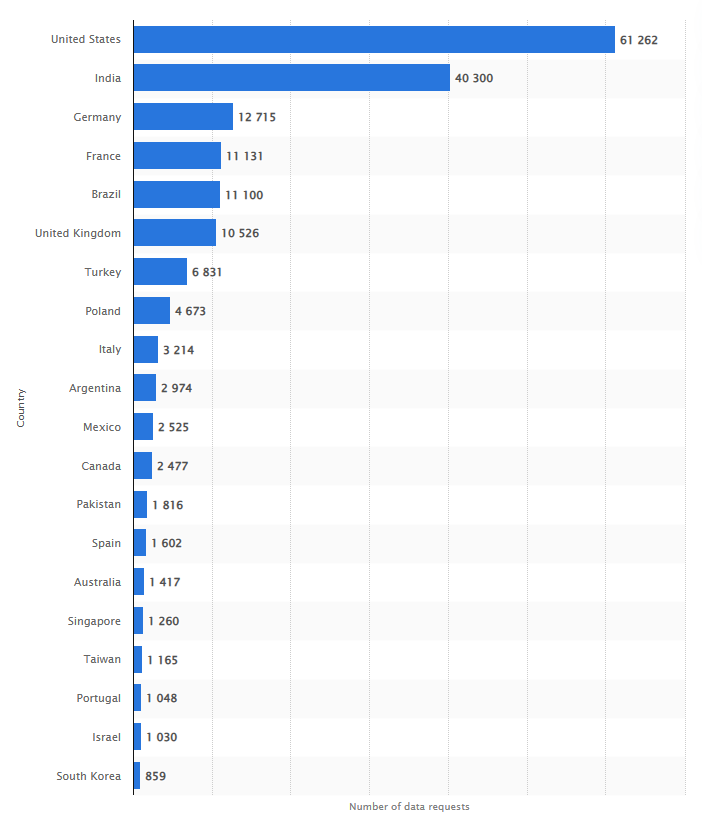
2021 showed a growth trajectory, with Facebook alone receiving 221,000 requests
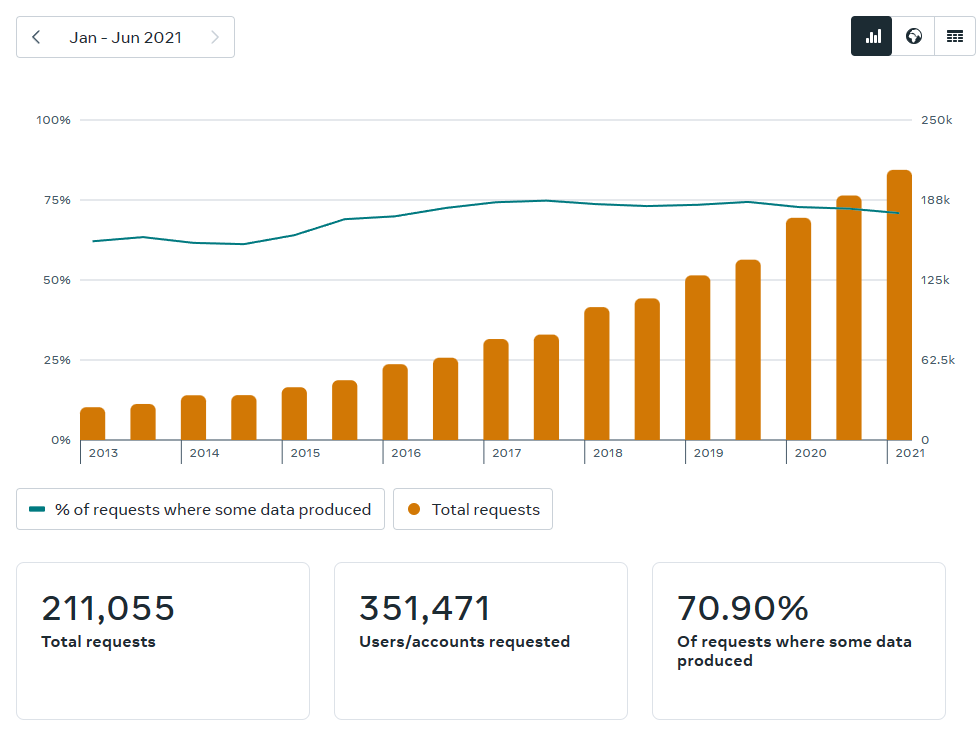
You can search for requests data points for your country at Government Requests for User Data | Transparency Center (fb.com)
Now some other things start making sense too!
Click!
There is a reason why China has already banned Facebook, WhatsApp, Quora etc., in favour of local variants, and the USA worked to ban Huawei, TikTok etc.
While this article focuses on the most well-regarded secure messaging app (WhatsApp), similar circumstances apply to popular messaging applications such as iMessage, etc.
Each Big Tech business stores several pieces of information about you, including:
- Activity
- Purchases
- Financial info
- Contact info
- Most used app functionality
- etc.
What can be done with all of this data and communications about you is of concern here.
Final thoughts
I cannot say I am surprised by the outcomes of my findings. I am also increasingly not surprised by the requests of governments to stop the adoption of E2EE or offer backdoor access:

What I am more surprised at is my surprise at how smooth the dots connected between the misdirection caused by the attack on E2EE while building such backdoor bridges that still give the necessary access legal entities need to do their work.
Conclusion
What started as an interest in the success of WhatsApp led me down a phenomenal rollercoaster ride exploring several stops along the way:
- What E2EE is and how it provides value (check out "Does your privacy matter? Why you may need to value E2EE (Non-Technical analysis)").
- The controversy around E2EE (check out "Does end-to-end encryption (E2EE) matter to you? Which side are you on?" and "Why I agree with end-to-end encryption (E2EE) - Let's discuss").
- The fuel behind the growth of WhatsApp (check out "WhatsApp: A whopping growth journey by the numbers, and what it means for you").
- Organisations continue to misdirect using noble causes and achieve what they need in an ever-changing world (check out "Surprise surprise! WhatsApp, Facebook Messenger, iMessage, government; life not so private after all! (P1)").
I hope this ride was equally informative and exciting!
I would love to learn more about your opinion on this!
Let me know….