How would you feel if:
- You are talking in private, and someone is overhearing what you are saying without your permission?
- Someone you do not know opens up your letters and reads them even before they arrive at your house?
- Someone intercepts your letters and changes their content to mean something else before they arrive at their final destination?
- You are sending your bank instructions to transact a payment, and someone changes both the amount and the destination of that transaction?
- You are sending agreements, contracts, photos in confidence to a trusted recipient to find them published on the internet without your express permission.

All of these are known as "Man in the middle" attacks, and lead to all type of trouble!
Digital is king now...
Digital communication has cemented itself as a primary way of sharing and reaching people both in private and business, globally. Our communication methods with people, partners, loved ones and partners are frequently done over email, text, phone and other platforms like Zoom and MS teams.
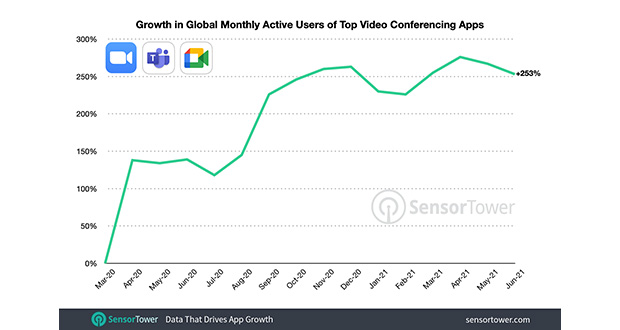
All tech platforms that enable communication and collaboration have registered a massive increase in their user base. This increase created additional intrigue in people to gain access to what others are sending and sharing (Secretly) or engage in cybercrime!
Extremely common
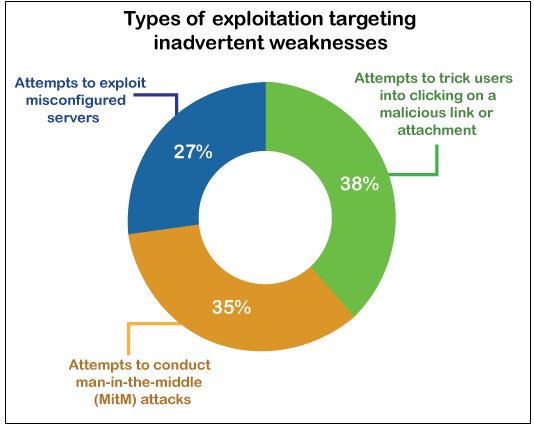
Man in the middle attacks is way more common than people think, tracking around 35% of methods used as a cybercrime attack. The increase also matches digital communications adoption in cyber-attacks, data breaches, and identity theft reports.

This is extremely important to you. Using a simple example, someone who steals your identity can contact your bank and initiate payments and transfers with the correct information.

Important contexts
Digital content
Digital content such as images, text, voice, video etc. are not designed to be secure:
- Email sends/receives messages in plain text.
- Messages and SMS also use plain text.
- Web content (images, music and video) are also, by default, unprotected.

The purpose of files and digital content formats (e.g. jpg, jpeg, mp3, mp4, Mkv, etc.) is to package information in the smallest amount of space possible to enable it to be sent/received between Point A and Point B using as little data as possible.
Our ability to transmit from Point A to Point B

They are designed this way because there are better solutions that are purposely built to send information and content from Point A to Point B as effectively and as securely as we may allow them to do.
We can imagine the ability to transmit data from Point A to Point B as communication pipes created through the magic wonders of networking and internet technology.
Content such as messages, audio, video etc., is then sent from Point A to Point B through these communication pipes.
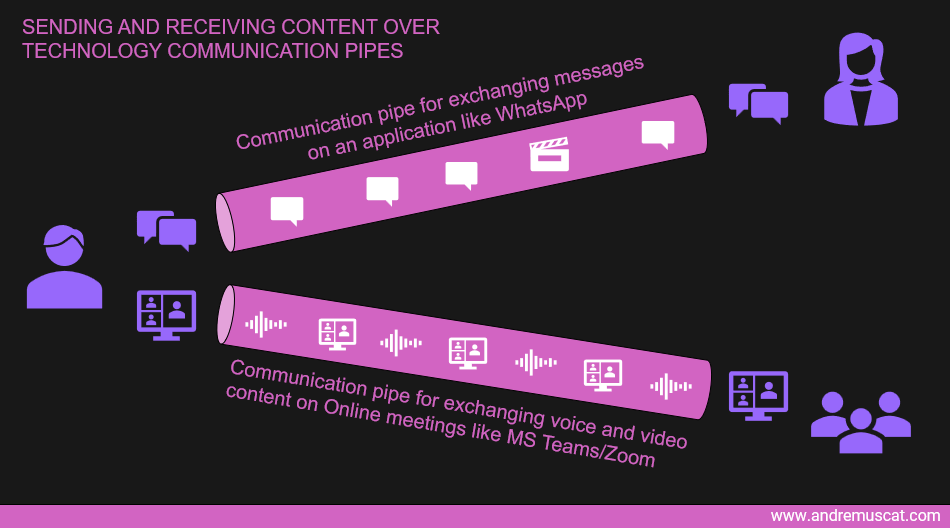
Cybercrime
When the internet started, these communication pipes were designed to transmit data from Point A to Point B simply.
The need to SECURE these pipes only originated from the impact of online attacks and cybercrime.
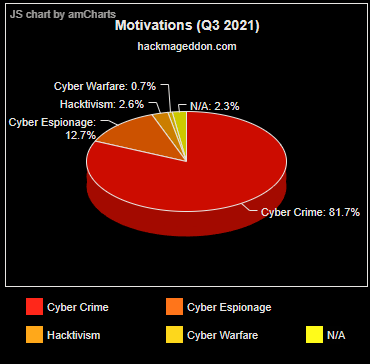
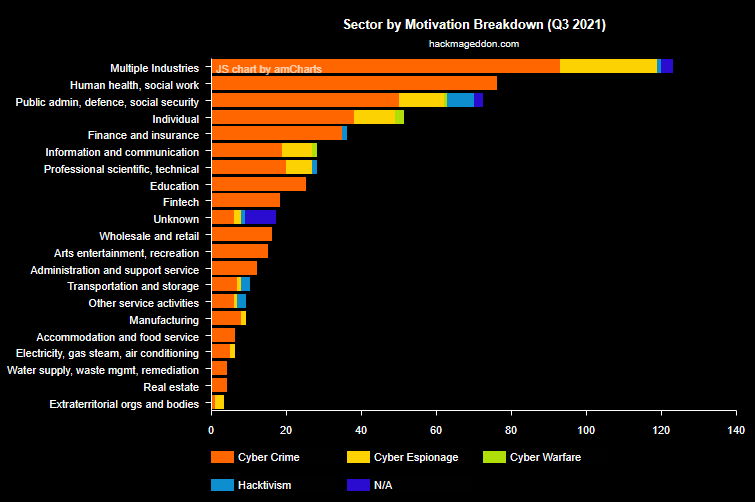
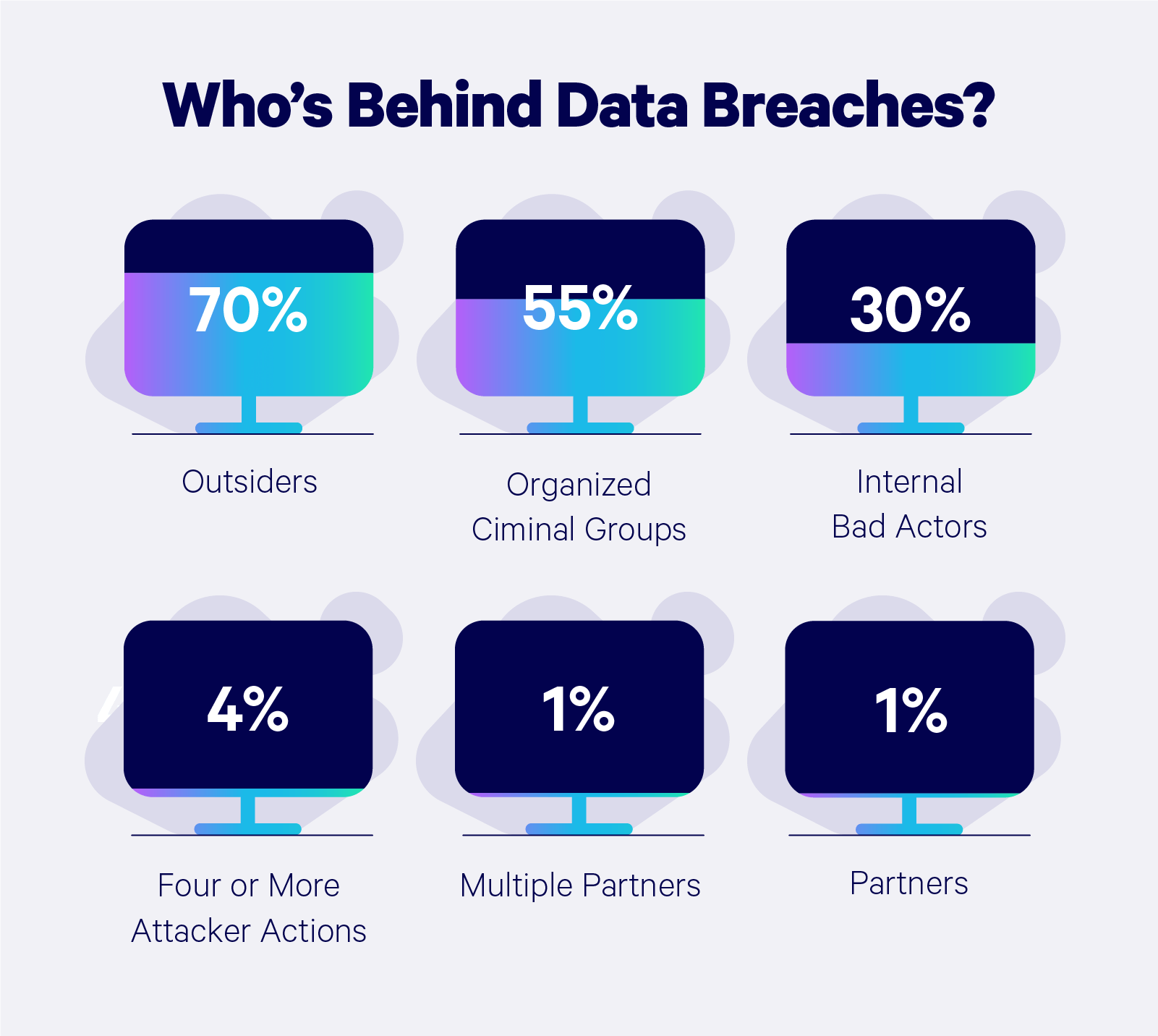
These attacks are of interest, especially in a context where
- 51% of cyber attacks are aimed at individuals, but only 14% are prepared to defend appropriately.
- Cybercriminals target individuals as relentlessly as they go after larger organisations.
- Cybercrime, cyber-espionage and malware are growing at accelerated speeds and impact. Data from Cloudwards indicates a 600% increase in cybercrime in the past 3 years.
- Cybercrime and other attacks are reporting increasing costs to remediate both personally and financially.
Enter the word Encryption...
Content relies on specialised security mechanisms to protect its integrity better. This is where content is placed in specialised containers engineered to HIDE information from prying eyes during transmission from Point A to Point B.

This is where hear technical terms like HTTPS be used. You indeed were told by someone that you should only trust websites that are using HTTPS. However, while this may be reasonable for web pages, more sophisticated methods are needed for real-time communications, such as
- Chat
- Team calls and meetings (Voice/Video)
- Social comms
- etc.
Keeping it simple, we use advanced methods collectively called Encryption to make normally accessible information into unreadable content unless otherwise authorised.
Enter the words End-to-End Encryption (E2EE)...
End-to-end Encryption (E2EE) describes the process of encrypting information being sent between Point A and B as part of a continuous communication stream. Its purpose is to ensure that only the sender and receiver can view the message's contents no matter the type of media transmitted (text, video, voice, audio, other etc.).
You may be already using E2EE today.

You most likely already use solutions that employ E2EE techniques such as:
- Mobile messaging apps like Signal, iMessage, WhatsApp and Telegram.
- Remote management software like Teamviewer.
We are now seeing a broader, more aggressive application with:
- Microsoft is deploying E2EE to its MS Teams.
- META (former Facebook) deploying it to its Instagram and Facebook Messenger.
- Zoom deploying it to its Meeting solutions.
But not everywhere
However, not everyone in Big tech is using E2EE yet, with many rushing to roll out broadly by the coming year.

NOTE: I realise that at the time of writing some companies like META (Former Facebook are in active development of such support, while others like MS Teams have recently started rolling it out.)
Using an example, Twitter does not use E2EE. This continues to be so even after it suffered several celebrity hacks and message leaks in recent years, including a massive Bitcoin scam involving accounts belonging to Elon Musk, Jeff Bezos, and Kanye West. To this day, direct Twitter messages between users are still not protected with E2EE, although Twitter is facing plenty of pressure to change its stance.
Enough of this geek-speak...why should you care?
As individuals, we generally welcome security upgrades that keep our communications private as we:
- Care about the integrity of our identity and our information.
- Value our privacy and initiatives that keep unwanted eyes from our content.
- Want to work in safe environments where our messages and materials remain integral to the communications we intend to send and receive.
- Aren't aware of the risks of our activities and the technologies we use.
- Cannot afford a dedicated cyber security team, often leaving us on our own to defend from personal attacks.
However, several events and emerging behaviours challenge the support for applying E2EE across applications in broader use.
Some organisations believe the loss of personal privacy (driven by Phone Tapping, Email Monitoring, etc.) is a viable strategy and acceptable sacrifice to battle terrorism and other malpractices.
This is a very sensitive topic and deserves more in-depth discussion.
Wrapping up
In this post, I set the stage around:
- What E2EE is
- Why it is important
- Where you may be already using it today
We also introduced the seeds of controversy being built around it.
In a future post, I will explore the arguments favouring or against applying this technology more deeply.
I am keen to find out more about your views. Reach out to hi@andremuscat.com today!